Are you looking for an article on how to monitor IDD users? Are you also looking for information what changes need to be made in order to achieve it? If yes, then refer this article. This article explains what is need of user monitoring and how to configure it.
DronaBlog
Tuesday, September 25, 2018
How to monitor what are users logged in to the Informatica Data Director Application?
Are you looking for an article on how to monitor IDD users? Are you also looking for information what changes need to be made in order to achieve it? If yes, then refer this article. This article explains what is need of user monitoring and how to configure it.
Sunday, September 23, 2018
Informatica Master Data Management - MDM - Quiz - 10
Q1. Match rule sets include which of the following
A. A search level that dictates the search strategy B. Any number of automatic and manual match column rules C. A filter to selectively include or exclude records from tha match batch D. Match path for inter-table/Intra-table-matchingQ2. Which correctly describes master data??
A. Customer name B. Customer address C. Customer purchases D. Customer preferencesQ3. A role is a set of privileges to access secure informatica MDM hub resources
A. True B. FalseQ4. Which statement best describes what the build match group(BMG) process does
A. Allows only a single "null to non-null" match into any group B. Removes redundant matching C. Executes in advance of the consolidate process D. All statements are correctQ5. What happens to records in the stage process that have structural integrity issues?
A. They are written to reject tables. B. They are placed in the manager merge process C. They are written to the raw table D. They are added to the enhanced filtering process for resolution. Previous Quiz Next QuizFriday, September 21, 2018
Informatica Master Data Management - MDM - Quiz - 9
Q1. Which of these features are supported in Metadata manager?
A. The renaming of certain design objects. B. Promoting record states. C. Running a simulation of applying a change List. D. Validate repository.
Q2. After configuration of the hub store which batch jobs are created automatically?
A. External Match jobs B. Revalidate Jobs C. Promote jobs D. Synchronize jobs
Q3. When grand children are displyaed in table, view all grand children are deplayed not just those related to the selected child.
A. True B. False
Q4. What does the trust frameWork do dynamically?
A. Defines whether two records will match B. Maintains cell-level survivor ship of only the best attributes C. Calculates a data quality score to be used on a data score card. D. Standardizes data to make its most trustworthy form.
Q5. Which of the following is NOT an advantage of the MDM hub?
A. Can run in any database and version. B. Flexibility to use any data model that is appropriate for a given customer. C. A consistent design and architecture built on a single code base. D. The ability to handle any data domain.
Previous Quiz Next Quiz
What is Hard Delete Detection in Informatica MDM?
What is the Hard Delete Detection?
What are the soft delete and the hard delete?
Do all types of databases support HDD in Informatica?
How HDD works in the Informatica MDM?
- The stage job in the MDM Hub compares all the records in the landing with the records in the previous landing table (aka PRL table) associated with each landing table.
- After determining the missing records in the landing table those are flagged as hard deletes for a full load.
- The hard delete flagged records are reinserted back into the landing table along with a delete flag value.
- For flagging records for hard deletes in the source, either we can use HUB_STATE_IND column or any other custom column.
- After running the stage and the load job in the MDM Hub, records are updated in the associated base object table.
What are the requirements for HDD implemenation?
- In order for HDD to work, we need to have a full load every time. It does not work with incremental or transitional loads.
- We need to create a hard delete detection table in the repository table to configure hard deletes.
- In order to make entry into the job metric table, we need to maintain an additional configuration.
- HDD requires user exits to be written in Java.
What are the User Exits required for HDD implementation?
Sample code for User Exits:
Wednesday, September 12, 2018
How to use 'grep' commands in Unix?
What is the 'grep' command?
The word grep stands for globally search a regular expression and print. The command 'grep' is a command-line utility. It is used for searching plain-text data. The search is performed by using a regular expression.Commands:
1. Use the command below to search a specific string in the specified filegrep "Techno Guru" test_file
2. Use the command below to search a specific string in all the files
grep "Techno Guru" *
3. Use the command below to search a specific string in only in the .log files. We can also use regular expressions such as abc*.log, *test*.*, abc*.log. Search will be performed against files which matches this file patterns.
grep "Techno Guru" *.log
4. Use the command below to perform case in-sensitive search. The command below will matches all the words such as "TECHNO GURU", "Techno Guru", "tEchno Guru", "techno guru" etc.
grep -i "Techno Guru" test_file
5. To print the matched line, along with 5 lines after it.
grep -A 5 -i "Techno Guru" test_file
6. To perform recursive search
grep -r "Techno Guru" test_file
7. To perform recursive search in all the files. Below command searches "Techno Guru" word in all the files under the current directory and its sub directory
grep -r "Techno Guru" *
8. Use the command below to search using regular expression in search string. The command below searches for starting string "Techno" and ends with "Guru". You can use other different search pattern as well.
grep "Techno*Guru" test_file
9. What are the regular patterns can be used?
The below mentioned regular patterns can be used while working with grep command.
? : Matched at most once.
* : Matched zero or more times.
+ : Matched one or more times.
{n} : Matched exactly n times.
{n,} : Matched n or more times.
{,m} : Matched at most m times.
{n,m} : Matched at least n times, but not more than m times.
10. Use 'grep -w' command to search for full words and not for sub-strings. In the below command exact "Techno" or "techno" or "TECHNO" will be matched in the file. However if file contains "Technoworld" then it will not be identified as match.
grep -iw "Techno" test_file
11. Displaying lines before/after/around the match using grep -A, -B and -C
If you are performing file analysis in real time project, it will be useful to see some lines after or before the match.
a) To display 5 lines after match
grep -A 5 -i "Techno Guru" test_file
b) To display 5 lines before match
grep -B 5 "Techno Guru" test_file
c) To display 4 lines around match. The option -C used for the match to be appeared with the lines from both the side.
grep -C 4 "Techno Guru" test_file
12. To count the number of matches use the command below
grep -c "Technology World" Test_file
13. To count the number lines which does NOT found match, use the command below
grep -v -c "Technology World" Test_file
14. To highlight the search. In order to see which part matches the line, we can highlight it as (Use can use any color to highlight)
export GREP_OPTIONS='--color=auto' GREP_COLOR='99;8'
15. To determine the name of files in which match string found.
grep -l "Techno" test_*
16. Use the command below to show only matched string as by default grep command shows the line which matches the given string.
grep -o "Techno Guru" Test_file
Learn more about Unix in the video below:
Monday, September 3, 2018
How to install Weblogic Server?
Step 1: Download weblogic server installer from Oracle website. If you downloaded on the Windows system then it will be .exe file. The first thing we need to create Weblogic server installation is the 'Domain. Double click on .exe file to launch it. You will get below dialog window where you need to provide domain name and location of domain. Provide these details and click on 'Next' button.
 |
Step 2: We need to create administrator user to perform administrator activities on weblogic server. To create admin user provide user name and password and optional description in the dialog window as shown in below screen shot and click on 'Next' button.
Step 10: In this step assign Admin Server and Manged servers to machine. Once assignment is done click on the 'Next' button.
Step 11: Assign JMS Services, Work manager and any other services to clusters or servers which are configured in earlier steps. Click on the 'Next' button.
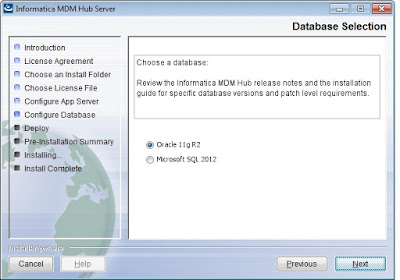
How to install Informatica MDM software?
Step 1: Locate the installer file, received from the Informatica Support team. In the Windows system, it will be .exe file. Double click on the .exe file. The dialog window will appear as shown in the screen below. Read the agreement and select the radio button corresponding to 'I accept the terms of the License Agreement' and then click on the 'Next' button.
Java Interview Questions and Answers - Part 4
Are you preparing for Java interview and looking for information for preparation? Are you also interested in knowing what kinds of questions about Object Oriented concepts are normally asked during Java interview? If so, then this article provides detailed questions and answers about Java, Object Oriented Concepts. This article also provides detailed information about Inheritance concepts. Good luck for your interview.
Q1: What is Object Oriented Programming?
Answer:
A programming style which is associated with the concepts like an object, a class, the inheritance, the polymorphism, an encapsulation and an abstraction is called as Object Oriented Programming.
Q2: What are the core concepts of Object Oriented Programming?
Answer:
 The core concepts of Object Oriented Programming are:
The core concepts of Object Oriented Programming are:- Inheritance
- Encapsulation
- Abstraction
- Polymorphism
Q3: What is inheritance?
Answer:
- Inheritance is nothing but inheriting properties (behaviour and state) of class into other class.
- The process by which one object acquires characteristics from one or more other objects is also termed as inheritance. e.g. children acquire characteristics from their parents.
- The class from which properties are inherited is called parent class or base class or superclass.
- The class in which properties are inherited is called child or derived class or subclass.
- It helps to reuse the code and establish a relationship between different classes.
- The common business logic can be moved from the derived class into the base class to improve maintainability of code.
Q4: What are types of inheritances?
Answer:
There are 4 types of inheritance1. Single Level Inheritance
2. Multi Level Inheritance
3. Hierarchical Inheritance
4. Hybrid Inheritance
Q5: Explain types of inheritances?
Answer:
1. Single Level Inheritance:a. In this type of inheritance, one class inherits the properties of the another class.
b. Properties such as behaviour and state from a single parent class is inherited in child class.
b. It helps to add new feature in existing code as as the code re-usability.
Here, Class Shape is parent class and Class Triangle is child class which inherits the properties and behaviour of the parent class.4
Class Shape
{ ... }
Class Triangle extends Shape
{ ... }
2. Multilevel Inheritance:
a. If class has more than one parent then it is called Multilevel Inheritance.
b. In the multilevel inheritance, a class is derived from the parent class which is also derived from another parent class.
Here, The class Square is derived from it's parent class Rectangle which is derived from it's parent Shape. The class Square has two parents - Rectangle and Shape respectively. Hence it is a multilevel inheritance.
Class Shape
{ ... }
Class Rectangle extends Shape
{ ... }
Class Square extends Rectangle
{ ... }
3. Hierarchical Inheritance:
a. In the hierarchical inheritance the parent class has more than one child classes.
b. We can also state that if more than one child classes have the same parent class then it is a hierarchical inheritance.
Here, the super class Shape has two sub classes - Triangle and Rectangle, hence it is a hierarchical inheritance.
Class Shape
{ ... }
Class Triangle extends Shape
{ ... }
Class Rectangle extends Shape
{ ... }
4. Hybrid Inheritance:
a. It is a combination of multiple inheritance and multilevel inheritance.
b. The multiple inheritance is not supported in Java as it leads to ambiguity.
c. Java supports multiple interfaces inheritance.
Q6: What is Implementation inheritance?
Answer:
a. Implementation inheritance is also know as class inheritance.b. We can extend an functionality by reusing functionality in the super class by inheriting all or some of the operations already implemented.
c. In Java, we can only inherit from one superclass.
d. It helps in code reusability.
e. Improper use of class inheritance can cause problem in making future changes.
f. The subclass becomes tightly coupled with the superclass.
g. We have to make sure that the subclasses depend only on the behavior of the superclass, not on the actual implementation.
Q7: What is Interface inheritance?
Answer:
a. Interface inheritance is also know as type inheritance or as subtyping.b. Interface inheritance reduces the coupling or implementation dependencies between systems.
c. It promotes the design concept of program to interfaces not to implementations.
d. We can implement any number of interfaces.
e. As this type of implementation will not influence specific subclass implementations, hence it is more flexible than implementation inheritance.
What are the Core Principles of Data Governance and How to Achieve Them?
In today's data-centric world, organizations are overwhelmed with vast volumes of data flowing from systems, apps, devices, and extern...

-
Are you looking for how to fix the error - "ORA-12801: error signaled in parallel query server P00D" in Oracle? Are you also inte...
-
Are you working on a project where the oracle database is being used for implementation? Are you also facing an ORA-00604 and looking for f...
-
Are you preparing for the Informatica MDM interview? Are you interested in knowing the questions normally asked during such an interview...